A breach that’s been on-going for months finally came to light on May 31, 2020, where a hacker stole and leaked data from the database of Daniel’s Hosting (DH).
DH was the largest free hosting provider on the Dark Web and housed various crypto-related stores and forums. The hacker obtained the data after breaching DH earlier this year.
Although reports show that DH is the home of illegal sites connected with cybercrime, it also hosts owners of political and dissident sites. These users prefer DH’s services since it protects their identities and prevents authorities from revealing them.
How Much Sensitive Data was Leaked Online?
According to DH’s reports, the hacked data includes 8,850 private keys of dark web (.onion) domains, 3,671 email addresses, and 7,205 passwords. The findings were confirmed by Under the Beach, a Threat Intelligence firm.
Users were warned after the breach to immediately change their passwords before creating new accounts with other hosting providers to prevent compromising the new sites.
According to the report, the leaked data contains sensitive information on darknet domain owners and users. The email addresses can be used to tie owners to specific .onion accounts.
What this Means for Illegal Darknet Sites
According to Under the Beach, the information released by the hacker could substantially help law enforcement departments. The data could help them track both the organizers of illegal activities and the participants on the Dark Websites.
Governments can also spot and follow the owners of dissident and political websites after their identities have been exposed. The anonymous and safe haven for whistleblowers and activists might have been compromised.
However, the hacker didn’t include IP addresses of the accounts, which would have made the investigations easier for law enforcement.
Previous Breaches
The hacker responsible for this activity and goes by the pseudonym KingNull claimed to be a part of the Anonymous collective.
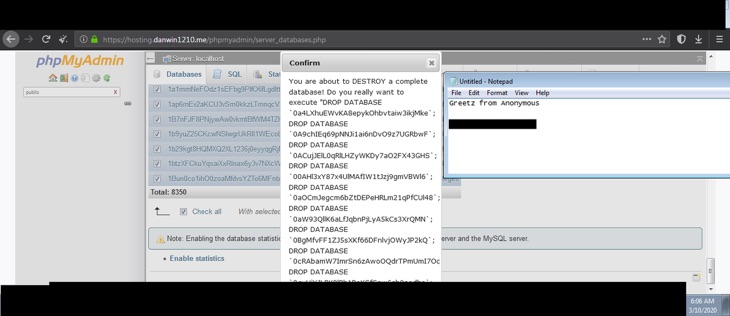
DH’s owner, Daniel Winzen, reported that when the hacker breached his portal on March 10, 2020, he stole its database, and then wiped all the servers. The hackers deleted all the databases that were connected to their hosting platform.
Two weeks later, Daniel’s Hosting shut down its services and urged users to move their websites to other dark web-hosting providers. More than 7,600 sites went down after DH’s shutdown – which represents a third of the dark web’s portals.
In a statement posted on the site before it went down, Daniel confirmed how the hacker might have gained full admin access to the site.
DH’s site was hacked earlier in November 2018, before the second breach in March 2020. An intruder, similar to KingNull, accessed the service’s backend database server and deleted all their websites. No data was leaked at the time, but over 6,500 sites were wiped clean.
Reference: The biggest data breaches and hacks since 2000
The Next Steps for DH
DH’s report clarified that while the hacker breached their database, their IP addresses weren’t stolen. Daniel Winzen stated that while they are working on handling things, they haven’t set a fixed date for relaunching the service.
Are You Hosting Your Site in a Vulnerable Environment?
It’s very likely that some genuine sites, on the grounds of privacy, might have their accounts hosted on Daniel’s Hosting. But privacy doesn’t always translate into security. These are two different things.
If you’d rather have private and secure hosting experiences, then you can use HostingGuruReviews.net’s unbiased review to your advantage. We use actual data from these hosting services’ servers, so you can monitor real server activities and use data-backed reviews to make better decisions.

